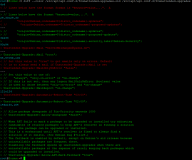
ich habe auf vielen VM's unattended-upgrades eingerichtet nach: https://wiki.debian.org/UnattendedUpgrades
Auf einer VM werden aber keine Updates installiert:
Code: Alles auswählen
root@forms:~$ unattended-upgrade -d
Skript für automatische Systemaktualisierung wird gestartet
Erlaubte Ursprünge sind: origin=Debian,codename=bullseye-updates, origin=Debian,codename=bullseye-proposed-updates, origin=Debian,codename=bullseye,label=Debian, origin=Debian,codename=bullseye,label=Debian-Security
Anfangsnegativliste:
Initial whitelist (not strict):
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/deb.debian.org_debian-security_dists_stable-security_main_i18n_Translation-en' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='' site='deb.debian.org' IndexType='Debian Translation Index' Size=201795 ID:11> with -32768 pin
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/deb.debian.org_debian-security_dists_stable-security_main_binary-amd64_Packages' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='amd64' site='deb.debian.org' IndexType='Debian Package Index' Size=287601 ID:10> with -32768 pin
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/security.debian.org_debian-security_dists_bullseye-security_main_i18n_Translation-en' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='' site='security.debian.org' IndexType='Debian Translation Index' Size=201795 ID:1> with -32768 pin
Marking not allowed <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/security.debian.org_debian-security_dists_bullseye-security_main_binary-amd64_Packages' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='amd64' site='security.debian.org' IndexType='Debian Package Index' Size=287601 ID:0> with -32768 pin
Applying pinning: PkgFilePin(id=11, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/deb.debian.org_debian-security_dists_stable-security_main_i18n_Translation-en' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='' site='deb.debian.org' IndexType='Debian Translation Index' Size=201795 ID:11>
Applying pinning: PkgFilePin(id=10, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/deb.debian.org_debian-security_dists_stable-security_main_binary-amd64_Packages' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='amd64' site='deb.debian.org' IndexType='Debian Package Index' Size=287601 ID:10>
Applying pinning: PkgFilePin(id=1, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/security.debian.org_debian-security_dists_bullseye-security_main_i18n_Translation-en' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='' site='security.debian.org' IndexType='Debian Translation Index' Size=201795 ID:1>
Applying pinning: PkgFilePin(id=0, priority=-32768)
Applying pin -32768 to package_file: <apt_pkg.PackageFile object: filename:'/var/lib/apt/lists/security.debian.org_debian-security_dists_bullseye-security_main_binary-amd64_Packages' a=stable-security,c=main,v=11,o=Debian,l=Debian-Security arch='amd64' site='security.debian.org' IndexType='Debian Package Index' Size=287601 ID:0>
Using (^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^linux-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^kfreebsd-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^gnumach-.*-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-modules-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$|^.*-kernel-[1-9][0-9]*\.[0-9]+\.[0-9]+-[0-9]+(-.+)?$) regexp to find kernel packages
Using (^linux-.*-5\.10\.0\-9\-amd64$|^linux-.*-5\.10\.0\-9$|^kfreebsd-.*-5\.10\.0\-9\-amd64$|^kfreebsd-.*-5\.10\.0\-9$|^gnumach-.*-5\.10\.0\-9\-amd64$|^gnumach-.*-5\.10\.0\-9$|^.*-modules-5\.10\.0\-9\-amd64$|^.*-modules-5\.10\.0\-9$|^.*-kernel-5\.10\.0\-9\-amd64$|^.*-kernel-5\.10\.0\-9$|^linux-.*-5\.10\.0\-9\-amd64$|^linux-.*-5\.10\.0\-9$|^kfreebsd-.*-5\.10\.0\-9\-amd64$|^kfreebsd-.*-5\.10\.0\-9$|^gnumach-.*-5\.10\.0\-9\-amd64$|^gnumach-.*-5\.10\.0\-9$|^.*-modules-5\.10\.0\-9\-amd64$|^.*-modules-5\.10\.0\-9$|^.*-kernel-5\.10\.0\-9\-amd64$|^.*-kernel-5\.10\.0\-9$) regexp to find running kernel packages
Checking: apache2 ([<Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'security.debian.org' isTrusted:True>, <Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'deb.debian.org' isTrusted:True>])
adjusting candidate version: apache2=2.4.48-3.1+deb11u1
Checking: apache2-bin ([<Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'security.debian.org' isTrusted:True>, <Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'deb.debian.org' isTrusted:True>])
adjusting candidate version: apache2-bin=2.4.48-3.1+deb11u1
Checking: apache2-data ([<Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'security.debian.org' isTrusted:True>, <Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'deb.debian.org' isTrusted:True>])
adjusting candidate version: apache2-data=2.4.48-3.1+deb11u1
Checking: apache2-utils ([<Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'security.debian.org' isTrusted:True>, <Origin component:'main' archive:'stable-security' origin:'Debian' label:'Debian-Security' site:'deb.debian.org' isTrusted:True>])
adjusting candidate version: apache2-utils=2.4.48-3.1+deb11u1
pkgs that look like they should be upgraded:
Fetched 0 B in 0s (0 B/s)
fetch.run() result: 0
Packages blacklist due to conffile prompts: []
Es wurden keine Pakete gefunden, von denen eine automatische Systemaktualisierung durchgeführt werden kann und kein ausstehendes automatisches Entfernen.
Package apache2 has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package apache2-bin has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package apache2-data has a higher version available, checking if it is from an allowed origin and is not pinned down.
Package apache2-utils has a higher version available, checking if it is from an allowed origin and is not pinned down.
Extracting content from /var/log/unattended-upgrades/unattended-upgrades-dpkg.log since 2021-10-15 07:18:54
root@forms:~$
Code: Alles auswählen
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";
Code: Alles auswählen
root@forms:~$ grep "^[^//]" /etc/apt/apt.conf.d/50unattended-upgrades
Unattended-Upgrade::Origins-Pattern {
// Codename based matching:
// This will follow the migration of a release through different
// archives (e.g. from testing to stable and later oldstable).
// Software will be the latest available for the named release,
// but the Debian release itself will not be automatically upgraded.
"origin=Debian,codename=${distro_codename}-updates";
//"origin=Debian,codename=${distro_codename}-proposed-updates";
"origin=Debian,codename=${distro_codename},label=Debian";
"origin=Debian,codename=${distro_codename},label=Debian-Security";
// Archive or Suite based matching:
// Note that this will silently match a different release after
// migration to the specified archive (e.g. testing becomes the
// new stable).
};
Unattended-Upgrade::Package-Blacklist {
// The following matches all packages starting with linux-
// Use $ to explicitely define the end of a package name. Without
// the $, "libc6" would match all of them.
// Special characters need escaping
// The following matches packages like xen-system-amd64, xen-utils-4.1,
// xenstore-utils and libxenstore3.0
// For more information about Python regular expressions, see
// https://docs.python.org/3/howto/regex.html
};
Unattended-Upgrade::Mail "root";
Unattended-Upgrade::MailOnlyOnError "false";
Unattended-Upgrade::Automatic-Reboot "true";
Unattended-Upgrade::Automatic-Reboot-Time "03:00";
root@forms:~$
Code: Alles auswählen
root@forms:~$ grep "^[^#;]" /etc/apt/sources.list
deb http://security.debian.org/debian-security bullseye-security main
deb http://deb.debian.org/debian stable main contrib non-free
deb http://deb.debian.org/debian-security stable-security main contrib non-free
root@forms:~$
Code: Alles auswählen
root@forms:~$ systemctl status unattended-upgrades
● unattended-upgrades.service - Unattended Upgrades Shutdown
Loaded: loaded (/lib/systemd/system/unattended-upgrades.service; enabled; vendor preset: enabled)
Active: active (running) since Thu 2021-10-14 06:07:47 CEST; 1 day 1h ago
Docs: man:unattended-upgrade(8)
Main PID: 2468242 (unattended-upgr)
Tasks: 2 (limit: 2337)
Memory: 8.6M
CPU: 67ms
CGroup: /system.slice/unattended-upgrades.service
└─2468242 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
Okt 14 06:07:47 forms.example.org systemd[1]: Started Unattended Upgrades Shutdown.
root@forms:~$